Global alert to prepare for fresh cyber attacks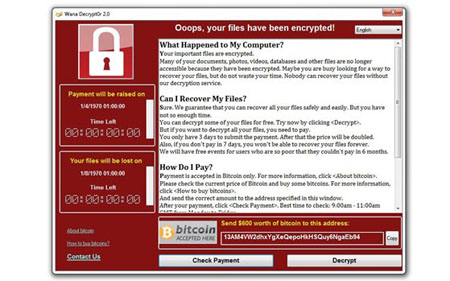 FT.com, May 15, 2017 by Sam Jones and Tim Bradshaw Businesses must brace for further cyber attacks this week on a potentially “significant scale”, British intelligence officials warned on Sunday, less than 48 hours after the debilitating WannaCry infection swept across the world. Current data show more than 1.3m computer systems are still vulnerable to infection by WannaCry, which has paralysed hospitals, disrupted transport networks and immobilised businesses, according to cyber security analysts. So far, 200,000 computers across 150 countries are known to have been infected in the first wave of the WannaCry cyber attack, Europol said on Sunday. “The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits,” the European police agency added. Intelligence agencies in Europe and the US have spent the weekend warning large companies and organisations that the threat from the ransomware — a category of malicious software that encrypts infected machines’ hard drives and demands payment to release the data again — may escalate. “We are aware of attempts to attack other UK centres beyond the health service,” Ciaran Martin, director of the National Cyber Security Centre, an arm of the electronic intelligence agency GCHQ, told the Financial Times. He said there was no evidence WannaCry had been updated by its creators to address the element in its coding that halted its spread late on Friday. Officials believe WannaCry is the creation of a criminal group. “With the National Crime Agency we have an aroundtheclock effort to work out who is responsible,” Mr Martin said. “We have a number of leads but we can’t comment on them.” Anthony Ferrante, a former director for Cyber Incident Response at the US National Security Council, thought the cyber attack was not yet over. “We could see some activity on Monday morning when people show up for work,” he said. The scale of the incident has prompted international coordination from governments and law enforcement. Mr Ferrante, managing director at FTI Consulting’s forensics and litigation unit, said the US government was taking the threat extremely seriously. US President Donald Trump ordered emergency White House meetings on Friday and Saturday to identify the culprits and the threat posed by the cyber attack, a White House official said. Mr Trump directed Tom Bossert, his homeland security adviser, to convene the meetings, which were attended by senior security staff from agencies including the FBI and National Security Agency The list of organisations hit by WannaCry has steadily lengthened: alongside Britain’s National Health Service, victims include the Deutsche Bahn, FedEx, Russia’s ministry of the interior, Renault, Telefónica and China National Petroleum Corp. Russia, Ukraine, India and Taiwan were the most seriously affected countries, according to cyber security company Kaspersky Lab. Despite urgent appeals for organisations to address the critical Windows software security vulnerability exploited by WannaCry, many still have not done so. “We all need to take responsibility for cyber security. We can’t just leave it to someone else to take care of.” According to cyber intelligence company Digital Shadows, more than 1.3m computers connected to the internet are vulnerable. “It’s only a matter of time before cyber criminals evolve the WannaCry ransomware malware to become even more virulent,” said Becky Pinkard, vicepresident of service delivery and intelligence at Digital Shadows. WannaCry’s potency is based on a cyber weapon known as EternalBlue, developed by the US National Security Agency. It was stolen and leaked online last year by a group known as the Shadow Brokers, believed by western intelligence to be connected to Russia’s spy agencies. EternalBlue, built by the NSA to exploit the thenunknown Windows software loophole, was used as a platform by WannaCry’s operators to supercharge their ransomware. The virus spread across organisations via any filesharing protocols, such as drop boxes for documents or databases. The spread of WannaCry was halted early on Friday thanks to the efforts of a British cyber security researcher, who works under the online pseudonym But he warned that the kill switch could easily be written out of a repurposed version of WannaCry. A senior British security official said the ransomware “The payload could have simply been a command to wipe the hard drive of the machine entirely,” he said. “That would have been devastating and it still could be.” |